The state of go in Vermont
The Birlington Free Press has a lengthy column on the popularity of go in the State of Virginia.
"'Vermont is really quite interesting in that we have about 15 regular members that come to the club,' said David Felcan, president of the Vermont Go Club. The club is the local chapter of the American Go Association, which, Felcan said, has about 2,100 members nationwide. 'In terms of per capita, Go in Vermont is huge,' he said."
inside the man
Saturday, July 30, 2005
Sunday, July 24, 2005
The Korea Times baduk lesson
The Korea Times is running an English language series of basic go lessons.

"In China, baduk is called 'weiqi,' which literally means the game of surrounding: to surround territory, and to surround the opponent's stones to capture them. To surround and capture your opponent's stones is a good way to gain territory, but it is just the means to an end. The ultimate object of baduk is to gain more territory through surrounding."
The Korea Times is running an English language series of basic go lessons.

"In China, baduk is called 'weiqi,' which literally means the game of surrounding: to surround territory, and to surround the opponent's stones to capture them. To surround and capture your opponent's stones is a good way to gain territory, but it is just the means to an end. The ultimate object of baduk is to gain more territory through surrounding."
Hacker Gary McKinnon interviewed
Slashot points out this interesting BBC interview with "famous" hacker Gary McKinnon. He claims, among other things, to have found evidence of the truth about UFOs on US computer systems - and he was smoking weed while discovering this proof.
"The BBC World Service has a half hour audio interview with British hacker Gary McKinnon. As recently reported on/. and BBC News, Gary was arrested and freed on bail pending extradition proceedings to the U.S.. There, he faces charges of gaining unauthorised access and causing criminal damage to military computers in his search for evidence of UFO coverups and anti-gravity technology of extra-terrestrial origin."
Slashot points out this interesting BBC interview with "famous" hacker Gary McKinnon. He claims, among other things, to have found evidence of the truth about UFOs on US computer systems - and he was smoking weed while discovering this proof.
"The BBC World Service has a half hour audio interview with British hacker Gary McKinnon. As recently reported on/. and BBC News, Gary was arrested and freed on bail pending extradition proceedings to the U.S.. There, he faces charges of gaining unauthorised access and causing criminal damage to military computers in his search for evidence of UFO coverups and anti-gravity technology of extra-terrestrial origin."
Friday, July 22, 2005
What we should do
A valuable thought from Schneier:
"I often get comments along the lines of 'Stop criticizing stuff; tell us what we should do.' My answer is always the same. Counterterrorism is most effective when it doesn't make arbitrary assumptions about the terrorists' plans. Stop searching bags on the subways, and spend the money on 1) intelligence and investigation -- stopping the terrorists regardless of what their plans are, and 2) emergency response -- lessening the impact of a terrorist attack, regardless of what the plans are. Countermeasures that defend against particular targets, or assume particular tactics, or cause the terrorists to make insignificant modifications in their plans, or that surveil the entire population looking for the few terrorists, are largely not worth it."
A valuable thought from Schneier:
"I often get comments along the lines of 'Stop criticizing stuff; tell us what we should do.' My answer is always the same. Counterterrorism is most effective when it doesn't make arbitrary assumptions about the terrorists' plans. Stop searching bags on the subways, and spend the money on 1) intelligence and investigation -- stopping the terrorists regardless of what their plans are, and 2) emergency response -- lessening the impact of a terrorist attack, regardless of what the plans are. Countermeasures that defend against particular targets, or assume particular tactics, or cause the terrorists to make insignificant modifications in their plans, or that surveil the entire population looking for the few terrorists, are largely not worth it."
Wednesday, July 20, 2005
Copyright polarization
The Register has a detailed piece analyzing all sides of the highly polarized copyright debate. Well worth reading.
"The debate is much more interesting than Yet Another Argument About Copyright because it reveals how people value human creativity, and that's something we're all entitled to have a say in. It also reveals what people really mean when they claim their position is 'good for society' - and again, it's our obligation when someone with this purpose pops up to shake them down vigorously, and see what rolls out of their trousers. In this case there is much merit on both sides of the exchange."
The Register has a detailed piece analyzing all sides of the highly polarized copyright debate. Well worth reading.
"The debate is much more interesting than Yet Another Argument About Copyright because it reveals how people value human creativity, and that's something we're all entitled to have a say in. It also reveals what people really mean when they claim their position is 'good for society' - and again, it's our obligation when someone with this purpose pops up to shake them down vigorously, and see what rolls out of their trousers. In this case there is much merit on both sides of the exchange."
Today's public service announcement
.jpg)
The American robin (QuickTime)
Courtesy of the Canadian Wildlife Service.
.jpg)
The American robin (QuickTime)
Courtesy of the Canadian Wildlife Service.
Thursday, July 14, 2005
One step closer to the open library system dream
I am extremely pleased that the open ils project has found a way to expose an XML interface for search and circulation functions. This creates unending potential for extensibility and integration with other applications - at least for large sophisticated library systems that are capable of taking advantage of these opportunities.
"So, after our discussion of XML and JSON in the previous post, Mike sat down and developed a REST style XML handler to the system. You pass in the same URL parameters and receive data/objects as XML instead of JSON. Now anyone who wishes to use an XML based client interface will have access to the same data and will retrieve it in the same way, except for the location they request in the URL. Allowing Apache plugins to do all of the conversion work for us (the XML plugin was about 120 lines Perl code) we can transform our system data into just about anything that Apache can serve."
You can review the open ils XML/AJAX/JSON debate here. Maybe you can change the world through blogging.
I am extremely pleased that the open ils project has found a way to expose an XML interface for search and circulation functions. This creates unending potential for extensibility and integration with other applications - at least for large sophisticated library systems that are capable of taking advantage of these opportunities.
"So, after our discussion of XML and JSON in the previous post, Mike sat down and developed a REST style XML handler to the system. You pass in the same URL parameters and receive data/objects as XML instead of JSON. Now anyone who wishes to use an XML based client interface will have access to the same data and will retrieve it in the same way, except for the location they request in the URL. Allowing Apache plugins to do all of the conversion work for us (the XML plugin was about 120 lines Perl code) we can transform our system data into just about anything that Apache can serve."
You can review the open ils XML/AJAX/JSON debate here. Maybe you can change the world through blogging.
Wednesday, July 13, 2005
Wi-fi bandits beware
Many people take a rather cavalier attitude towards hopping onto whatever unprotected wireless network might be at hand. You might want to rethink your perspective based on this news item blogged today by Schneier.
"Near as I can tell, there was no other criminal activity involved. The man who used someone else's wireless wasn't doing anything wrong with it; he was just using the Internet."
Of course, there are many wireless network owners that leave their networks open precisely because they do not mind at all if passers by jump on for a while. I am sure that I am not the first to suggest this, but if you have no problem with casual users on your network, broadcast a clearly inviting SSID such as "all_r_welcome".
Many people take a rather cavalier attitude towards hopping onto whatever unprotected wireless network might be at hand. You might want to rethink your perspective based on this news item blogged today by Schneier.
"Near as I can tell, there was no other criminal activity involved. The man who used someone else's wireless wasn't doing anything wrong with it; he was just using the Internet."
Of course, there are many wireless network owners that leave their networks open precisely because they do not mind at all if passers by jump on for a while. I am sure that I am not the first to suggest this, but if you have no problem with casual users on your network, broadcast a clearly inviting SSID such as "all_r_welcome".
Saturday, July 09, 2005
Anonymity of press sources - the greater good?
New York Times reporter Judith Miller is in jail for not giving up her source.
"Miller talked to sources about the leak, but never wrote a news story about the CIA operative. By the time she was ushered off to jail, there seemed little need for her testimony because at least one, and likely both reporters who actually did write stories naming Plame had already agreed to talk.
Time magazine reporter Matthew Cooper also faced the grim prospect of jail on Wednesday. But his employer had already ignominiously folded and given notes identifying his source to Special Prosecutor Patrick Fitzgerald. Then Cooper's source released him from his promise of confidentiality, freeing him to testify before the grand jury.
Syndicated columnist Robert Novak also identified Plame in print. He has refused to say whether he gave up his confidential source to Fitzgerald, but it's telling that he was not facing jail Wednesday along with Miller and Cooper."
New York Times reporter Judith Miller is in jail for not giving up her source.
"Miller talked to sources about the leak, but never wrote a news story about the CIA operative. By the time she was ushered off to jail, there seemed little need for her testimony because at least one, and likely both reporters who actually did write stories naming Plame had already agreed to talk.
Time magazine reporter Matthew Cooper also faced the grim prospect of jail on Wednesday. But his employer had already ignominiously folded and given notes identifying his source to Special Prosecutor Patrick Fitzgerald. Then Cooper's source released him from his promise of confidentiality, freeing him to testify before the grand jury.
Syndicated columnist Robert Novak also identified Plame in print. He has refused to say whether he gave up his confidential source to Fitzgerald, but it's telling that he was not facing jail Wednesday along with Miller and Cooper."
Monday, July 04, 2005
Lee Sedol of Korea reclaims Fujitsu Cup
Go / weiqi / baduk news: Lee Sedol 9 dan of Korea defeated Choi Cheolhan 9 dan also of Korea to win the 18th international Fujitsu Cup. This is Lee Sedol's third Fujitsu Cup win in four years. View the game record here.
Go / weiqi / baduk news: Lee Sedol 9 dan of Korea defeated Choi Cheolhan 9 dan also of Korea to win the 18th international Fujitsu Cup. This is Lee Sedol's third Fujitsu Cup win in four years. View the game record here.
Saturday, July 02, 2005
AJAX + JSON - XML = AJAJ?
It might be fun, but is it a good idea? The open-ils project has been proud of its AJAX-like architecture with a twist - they see XML as too heavy so they use JSON. (AJAJ?)
"We've taken XMLHTTPRequest one step further and added JSON to the mix. JSON (mentioned in this blog previously) is a 'lightweight data-interchange format' (see json.org). It gives us a way to turn program objects into strings, or serialize them. JSON is great for us because it's a lot lighter than XML. It allows us to encode our data with practically no extraneous data clogging the lines. As a quick example, an array converted to JSON would look something like this: [ 1, 2, 3]. Whereas in XML it might appear like so: <array> <item>1</item> <item>2</item> <item>3</item> </array>. Even with a small dataset you see an immediate difference in the number of characters required to encode the object."
I am not quite sure what to make of this. It reminds me of a number of conversations that I have had mainly with older more experienced colleagues who approach me to explain the "XML thing" to them. Almost invariably, they are horrified at the overhead that XML carries with it. Almost invariably, I try to explain that it is worth it.
The open-ils team has also extended JSON with something they call "class hints".
"JSON parsers exist in many languages, and we've developed our own parsers in C, Perl, and Javascript. Why did we write our own, you ask? You guessed it - we took JSON one step further as well. We added what we call class hints to the JSON format. This allows us to parse a JSON string and determine what type of object we're looking at based on a hint encoded as a comment within the object. So, for example, the Javascript JSON parser might receive a JSON string from the server that is encoded with a class hint of 'user'. The JSON parser will then be able to turn the JSON string into a full blown Javascript 'user' object that knows how to access and update the data it contains."
It goes without saying that had they stuck with XML, all of their data objects would have been self describing. In fact, they had to break the JSON standard precisely because it is too concise to be self describing. Was it worth it? Are the open-ils guys and gals just being conservative in putting data optimization before usability, or are they on to something that the AJAX crowd is missing?
It might be fun, but is it a good idea? The open-ils project has been proud of its AJAX-like architecture with a twist - they see XML as too heavy so they use JSON. (AJAJ?)
"We've taken XMLHTTPRequest one step further and added JSON to the mix. JSON (mentioned in this blog previously) is a 'lightweight data-interchange format' (see json.org). It gives us a way to turn program objects into strings, or serialize them. JSON is great for us because it's a lot lighter than XML. It allows us to encode our data with practically no extraneous data clogging the lines. As a quick example, an array converted to JSON would look something like this: [ 1, 2, 3]. Whereas in XML it might appear like so: <array> <item>1</item> <item>2</item> <item>3</item> </array>. Even with a small dataset you see an immediate difference in the number of characters required to encode the object."
I am not quite sure what to make of this. It reminds me of a number of conversations that I have had mainly with older more experienced colleagues who approach me to explain the "XML thing" to them. Almost invariably, they are horrified at the overhead that XML carries with it. Almost invariably, I try to explain that it is worth it.
The open-ils team has also extended JSON with something they call "class hints".
"JSON parsers exist in many languages, and we've developed our own parsers in C, Perl, and Javascript. Why did we write our own, you ask? You guessed it - we took JSON one step further as well. We added what we call class hints to the JSON format. This allows us to parse a JSON string and determine what type of object we're looking at based on a hint encoded as a comment within the object. So, for example, the Javascript JSON parser might receive a JSON string from the server that is encoded with a class hint of 'user'. The JSON parser will then be able to turn the JSON string into a full blown Javascript 'user' object that knows how to access and update the data it contains."
It goes without saying that had they stuck with XML, all of their data objects would have been self describing. In fact, they had to break the JSON standard precisely because it is too concise to be self describing. Was it worth it? Are the open-ils guys and gals just being conservative in putting data optimization before usability, or are they on to something that the AJAX crowd is missing?
Friday, July 01, 2005
Google Maps icons
I just completed my first hack with the new Google Maps API. It is a work in progress supporting my daughter's fundraising hikes in Elk Island National Park (click the static image below to go to the interactive map).
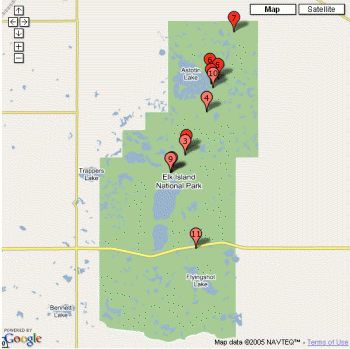
The new API is very slick and easy to work with. The one area of complexity is around custom icons. Although it is well documented in the API docs, I discovered this complexity when I wanted to use two colors of numbered markers in place the of the standard "pinkish" lettered markers used by Google (RTFM, Chris). To save myself much grief, I created my own set of pink and red numbered markers based on the pinky lettered Google ones. This way I could rely on the default shadow images and other icon defaults. And here they are for you to use too.
























Requests to the web community and/or Google:
I just completed my first hack with the new Google Maps API. It is a work in progress supporting my daughter's fundraising hikes in Elk Island National Park (click the static image below to go to the interactive map).

The new API is very slick and easy to work with. The one area of complexity is around custom icons. Although it is well documented in the API docs, I discovered this complexity when I wanted to use two colors of numbered markers in place the of the standard "pinkish" lettered markers used by Google (RTFM, Chris). To save myself much grief, I created my own set of pink and red numbered markers based on the pinky lettered Google ones. This way I could rely on the default shadow images and other icon defaults. And here they are for you to use too.
Requests to the web community and/or Google:
- Someone needs to build a repository of freely accessible Google Maps icons, including the necessary shadow images, image maps, and JavaScript constructor code in order to properly use the icons.
- Someone needs to build a Google Map polyline drawer as I, for one, would rather trace polylines using my mouse than hand code the points on a path.
Subscribe to:
Posts (Atom)
Blog Archive
-
▼
2005
(228)
-
▼
July
(12)
- The state of go in Vermont The Birlington Free Pr...
- The Korea Times baduk lessonThe Korea Times is run...
- Hacker Gary McKinnon interviewedSlashot points out...
- What we should do A valuable thought from Schneie...
- Copyright polarization The Register has a detaile...
- Today's public service announcementThe American ro...
- One step closer to the open library system dreamI ...
- Wi-fi bandits beware Many people take a rather c...
- Anonymity of press sources - the greater good?New ...
- Lee Sedol of Korea reclaims Fujitsu CupGo / weiqi ...
- AJAX + JSON - XML = AJAJ? It might be fun, but is ...
- Google Maps iconsI just completed my first hack wi...
-
▼
July
(12)
About Me
- thrashor
- Edmonton, Alberta, Canada
- Returned to working as a Management Consultant, specializing in risk, security, and regulatory compliance, with Fujitsu Canada after running the IT shop in the largest library in the South Pacific.
